I’m working on this.
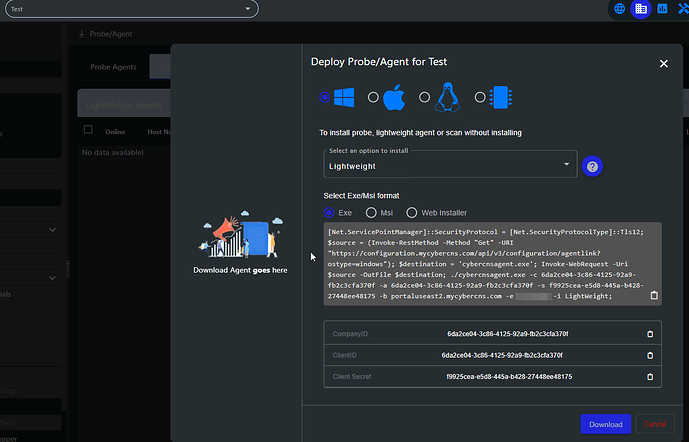
When you create the download link for the agent through ConnectSecure, it will expire in 24 hours.
I couldn’t find the API endpoint in the ConnectSecure documentation for generating the download link. However, by scraping it, I managed to find the endpoint.
In case you need it, here is the endpoint:
https://configuration.myconnectsecure.com/api/v4/configuration/agentlink?ostype=windows
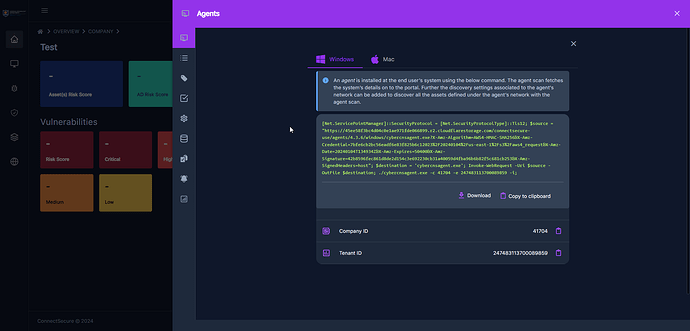
Installation: Connect Secure Setup Install Script
# $ArgumentList = @(
# "-c $CompanyID",
# "-a $ClientID",
# "-i $InstallationType"
# )
$Arguments = "-c $CompanyID -e $ClientID -i $InstallationType"
$Process = Start-Process -Wait $InstallerFile -ArgumentList $Arguments -Passthru
Write-Host "ExitCode: $($Process.ExitCode)"
Uninstallation: Connect Secure Uninstallation Script
cd "C:\PROGRA~2"
sc stop ConnectSecureAgentMonitor
timeout /T 5 > nul
sc delete ConnectSecureAgentMonitor
timeout /T 5 > nul
sc stop CyberCNSAgent
timeout /T 5 > nul
sc delete CyberCNSAgent
ping 127.0.0.1 -n 6 > nul
taskkill /IM osqueryi.exe /F
taskkill /IM nmap.exe /F
taskkill /IM cyberutilities.exe /F
taskkill /IM cybercnsagent.exe /F
CyberCNSAgent\cybercnsagent.exe --internalAssetArgument uninstallservice
rmdir CyberCNSAgent /s /q
Configuration Task : Connect Secure Configuration Task
param(
[Parameter(Position=0,Mandatory=$True,HelpMessage=@'
-c, --companyId string CompanyID
'@)]
[String]$CompanyID,
[Parameter(Position=1,Mandatory=$True,HelpMessage=@'
-e, --tenantId string TenantID
'@)]
[String]$ClientID,
[Parameter(Position=2,Mandatory=$False,HelpMessage=@'
-i, --installAgent Install Agent
--internalAssetArgument string For Agent Internal Usage
'@)]
[ValidateSet('Probe','Lightweight')]
[String]$InstallationType='Lightweight'
)
Dynamic Versions: ConnectSecure Agent Dynamic Versions
Get-DynamicVersionsFromUrl `
-URL 'https://configuration.myconnectsecure.com/api/v4/configuration/agentlink?ostype=windows' `
-VersionsURLPattern '(?<Uri>https://.*.cloudflarestorage.com/connectsecure-use/agents/(?<Version>[\d\.]+)/windows/(?<FileName>cybercnsagent.exe)[^""]*)'